A technical paper titled “Security Verification of Low-Trust Architectures” was published by researchers at Princeton University, University of Michigan, and Lafayette College.
摘要:
“Low-trust architectures work on, from the viewpoint of software, always-encrypted data, and significantly reduce the amount of hardware trust to a small software-free enclave component. In this paper, we perform a complete formal verification of a specific low-trust architecture, the Sequestered Encryption (SE) architecture, to show that the design is secure against direct data disclosures and digital side channels for all possible programs. We first define the security requirements of the ISA of SE low-trust architecture. Looking upwards, this ISA serves as an abstraction of the hardware for the software, and is used to show how any program comprising these instructions cannot leak information, including through digital side channels. Looking downwards this ISA is a specification for the hardware, and is used to define the proof obligations for any RTL implementation arising from the ISA-level security requirements. These cover both functional and digital side-channel leakage. Next, we show how these proof obligations can be successfully discharged using commercial formal verification tools. We demonstrate the efficacy of our RTL security verification technique for seven different correct and buggy implementations of the SE architecture.”
找出 技术论文在这里。 2023 年 XNUMX 月出版(预印本)。
Tan, Qinhan, Yonathan Fisseha, Shibo Chen, Lauren Biernacki, Jean-Baptiste Jeannin, Sharad Malik, and Todd Austin. “Security Verification of Low-Trust Architectures.” arXiv preprint arXiv:2309.00181 (2023).
相关阅读
安全保障验证与测试
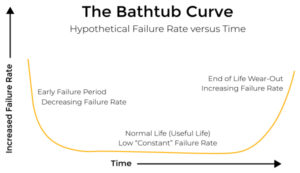
功能验证正在超出其能力范围,以确保系统安全可靠。 新的支持来自硬件和软件。
安全验证所需的新概念
为什么确保硬件正常工作并能够检测现场可能出现的漏洞如此困难。
- SEO 支持的内容和 PR 分发。 今天得到放大。
- PlatoData.Network 垂直生成人工智能。 赋予自己力量。 访问这里。
- 柏拉图爱流。 Web3 智能。 知识放大。 访问这里。
- 柏拉图ESG。 汽车/电动汽车, 碳, 清洁科技, 能源, 环境, 太阳能, 废物管理。 访问这里。
- 柏拉图健康。 生物技术和临床试验情报。 访问这里。
- 图表Prime。 使用 ChartPrime 提升您的交易游戏。 访问这里。
- 块偏移量。 现代化环境抵消所有权。 访问这里。
- Sumber: https://semiengineering.com/formal-verification-of-a-sequestered-encryption-architecture/
- :是
- $UP
- 2023
- a
- 抽象化
- 驳
- 所有类型
- 量
- an
- 和
- 任何
- 架构
- AS
- At
- 奥斯汀
- BE
- 作为
- 超越
- 都
- by
- CAN
- 不能
- 能力
- 能力
- 通道
- 陈
- 学院
- 未来
- 商业的
- 完成
- 元件
- 包括
- 概念
- 正确
- 外壳
- data
- 定义
- 演示
- 设计
- 不同
- 难
- 数字
- 直接
- 披露
- 功效
- 飞地
- 加密
- 确保
- 部分
- 姓氏:
- 针对
- 正式
- 止
- 实用
- 硬件
- 相关信息
- 创新中心
- HTTPS
- 履行
- 实现
- in
- 包含
- 信息
- 说明
- 它的
- 劳伦
- 泄漏
- 寻找
- 可能..
- 密歇根州
- 全新
- 下页
- 债券
- of
- on
- 我们的
- 纸类
- 演出
- 柏拉图
- 柏拉图数据智能
- 柏拉图数据
- 可能
- 普林斯顿
- 曲目
- 训练课程
- 证明
- 出版
- 减少
- 必须
- 岗位要求
- 研究人员
- 安全
- 实现安全
- 安全
- 保安
- 九月
- 服务
- XNUMX所
- 显示
- 侧
- 显著
- 小
- So
- 软件
- 具体的
- 规范
- 顺利
- SUPPORT
- 产品
- 文案
- test
- 这
- 博曼
- Free Introduction
- 通过
- 标题
- 至
- 工具
- 信任
- 大学
- 密歇根大学
- 向上
- 用过的
- 运用
- 企业验证
- 漏洞
- 是
- we
- 工作
- 合作
- 和风网