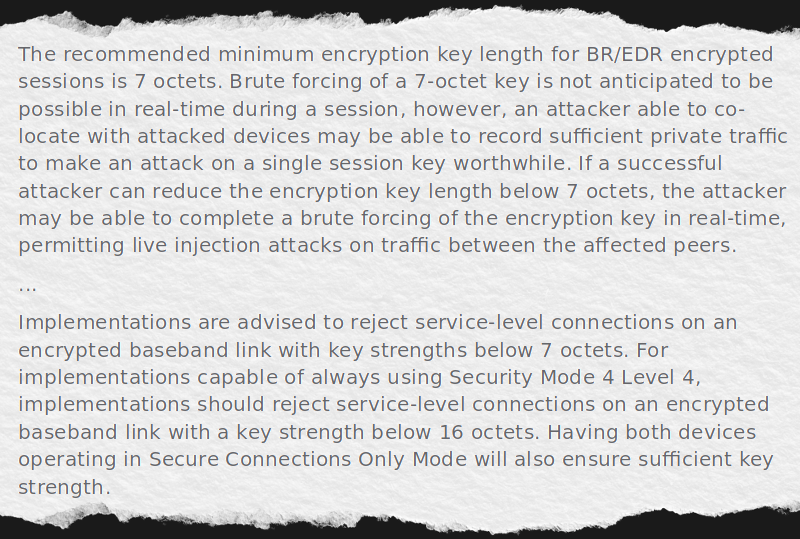
As we first reported in yesterday’s weekly security post, researchers at EURECOM have ujawnił szczegóły (PDF, referencje) of a new man-in-the-middle (MITM) attack on Bluetooth 4.2 through 5.4, which has been assigned CVE-2023-24023, Jak preceding CVEs, it concerns the session authentication between Bluetooth devices, where the attacker uses spoofed paired or bonded devices to force the use of a much shorter encryption key length.
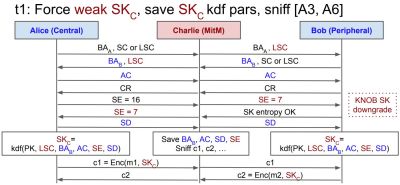 The name of this newly discovered vulnerability is BLUFFS (Bluetooth Forward and Future Secrecy), where forward and future secrecy are important terms that refer to the protection of secure sessions against compromise in the past (forward, FoS) and future (FuS). The CVE presentation notes that the Bluetooth specification does not cover either FuS or FoS. In total two new architectural vulnerabilities were discovered, both of which attack the security key.
The name of this newly discovered vulnerability is BLUFFS (Bluetooth Forward and Future Secrecy), where forward and future secrecy are important terms that refer to the protection of secure sessions against compromise in the past (forward, FoS) and future (FuS). The CVE presentation notes that the Bluetooth specification does not cover either FuS or FoS. In total two new architectural vulnerabilities were discovered, both of which attack the security key.
Bluetooth SIG ma Wydało oświadczenie regarding this attack method. Although serious, it would seem that the core issue is that some implementations allow for encryption key lengths below 7 octets:
Although the researchers note potential fixes and mitigations, these would need to be implemented in every affected Bluetooth controller out there — this might be a good time to re-examine in how far one relies on Bluetooth security, and what the effect of a hijacked session might be.
- Dystrybucja treści i PR oparta na SEO. Uzyskaj wzmocnienie już dziś.
- PlatoData.Network Pionowe generatywne AI. Wzmocnij się. Dostęp tutaj.
- PlatoAiStream. Inteligencja Web3. Wiedza wzmocniona. Dostęp tutaj.
- PlatonESG. Węgiel Czysta technologia, Energia, Środowisko, Słoneczny, Gospodarowanie odpadami. Dostęp tutaj.
- Platon Zdrowie. Inteligencja w zakresie biotechnologii i badań klinicznych. Dostęp tutaj.
- Źródło: https://hackaday.com/2023/12/02/update-on-the-bluffs-bluetooth-vulnerability/
- :ma
- :Jest
- :nie
- :Gdzie
- 1
- 116
- 7
- a
- ACM
- afektowany
- przed
- dopuszczać
- Chociaż
- i
- architektoniczny
- SĄ
- przydzielony
- At
- atakować
- Uwierzytelnianie
- BE
- być
- poniżej
- pomiędzy
- Bluetooth
- obie
- kompromis
- Obawy
- kontroler
- rdzeń
- pokrywa
- urządzenia
- odkryty
- robi
- efekt
- bądź
- szyfrowanie
- Każdy
- daleko
- i terminów, a
- poprawki
- W razie zamówieenia projektu
- wytrzymałość
- Naprzód
- przyszłość
- GitHub
- dobry
- Have
- W jaki sposób
- HTTPS
- wdrożenia
- realizowane
- ważny
- in
- problem
- IT
- jpg
- Klawisz
- Długość
- lubić
- Maksymalna szerokość
- metoda
- może
- MITM
- dużo
- Nazwa
- Potrzebować
- Nowości
- nowo
- nist
- noty
- of
- on
- ONE
- or
- na zewnątrz
- sparowany
- Przeszłość
- plato
- Analiza danych Platona
- PlatoDane
- potencjał
- presentation
- ochrona
- odnosić się
- w sprawie
- Zgłoszone
- Badacze
- bezpieczne
- bezpieczeństwo
- wydać się
- poważny
- Sesja
- Sesje
- kilka
- specyfikacja
- REGULAMIN
- że
- Połączenia
- Tam.
- Te
- to
- Przez
- czas
- do
- Kwota produktów:
- drugiej
- Aktualizacja
- posługiwać się
- zastosowania
- Luki w zabezpieczeniach
- wrażliwość
- we
- tygodniowy
- były
- Co
- który
- by
- zefirnet