A nuvem híbrida se tornou a dominant approach for enterprise cloud strategies, but it comes with complexity and concerns over integration, security and skills. To address these concerns the industry is embracing container runtime environments to abstract away infrastructure. Red Hat OpenShift Container Platform (RH OCP) surgiu como um leading solution for supporting the application development lifecycle, provisioning and managing container images and workloads into a platform for containerized applications and ecosystem. RH OCP provides a common deployment, control and management environment for workloads across a diverse set of infrastructures that underpin a hybrid cloud.
In brief, Red Hat OpenShift is the leading hybrid cloud application platform built on open-source innovation designed to build, deploy and run applications at massive scale, wherever you want.
Hybrid cloud is also forcing a significant rethinking of how to secure and protect data and assets. As such, the industry continues to move away from traditional moat-and-castle strategies towards zero trust-based architectures that micro-segment environments to minimize attack surfaces.
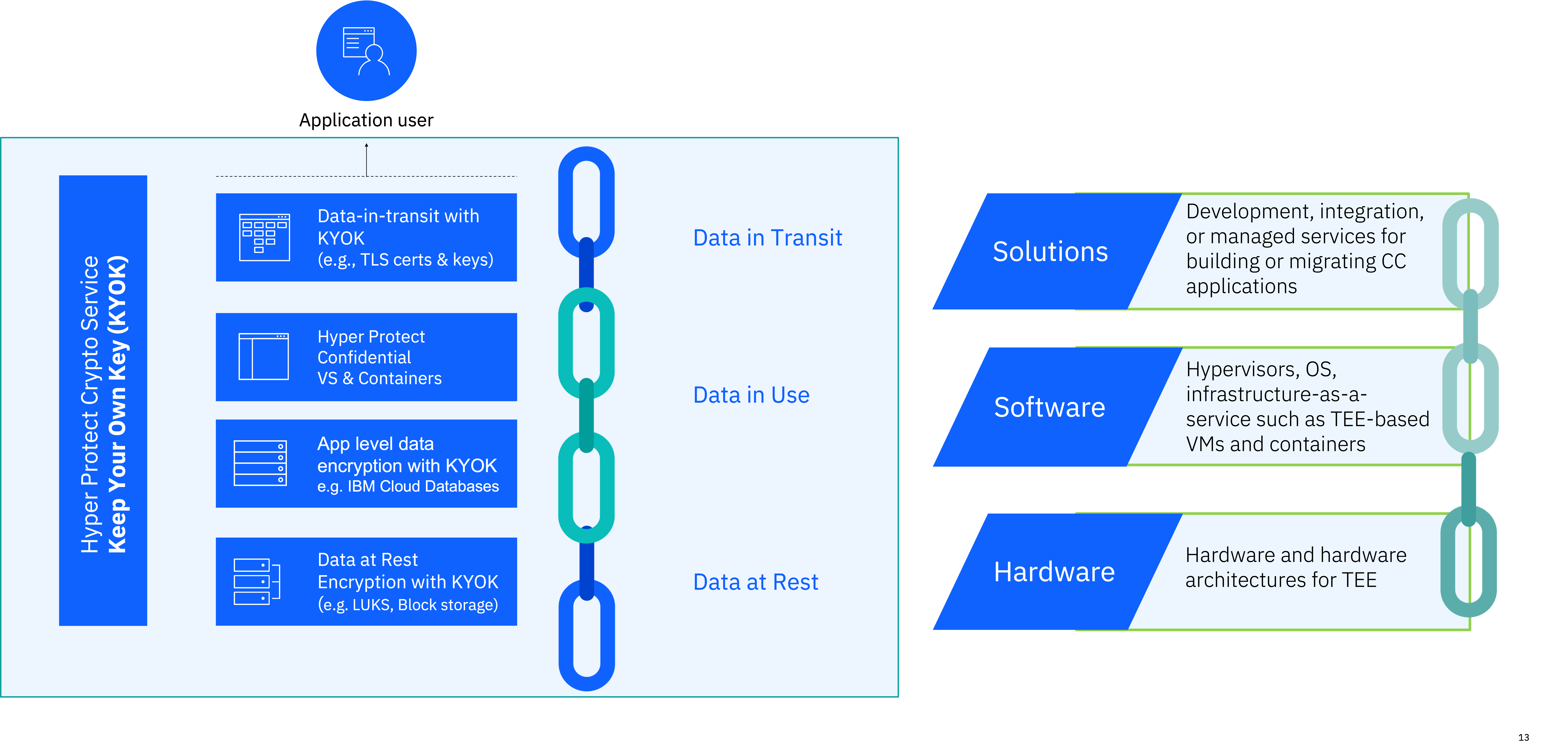
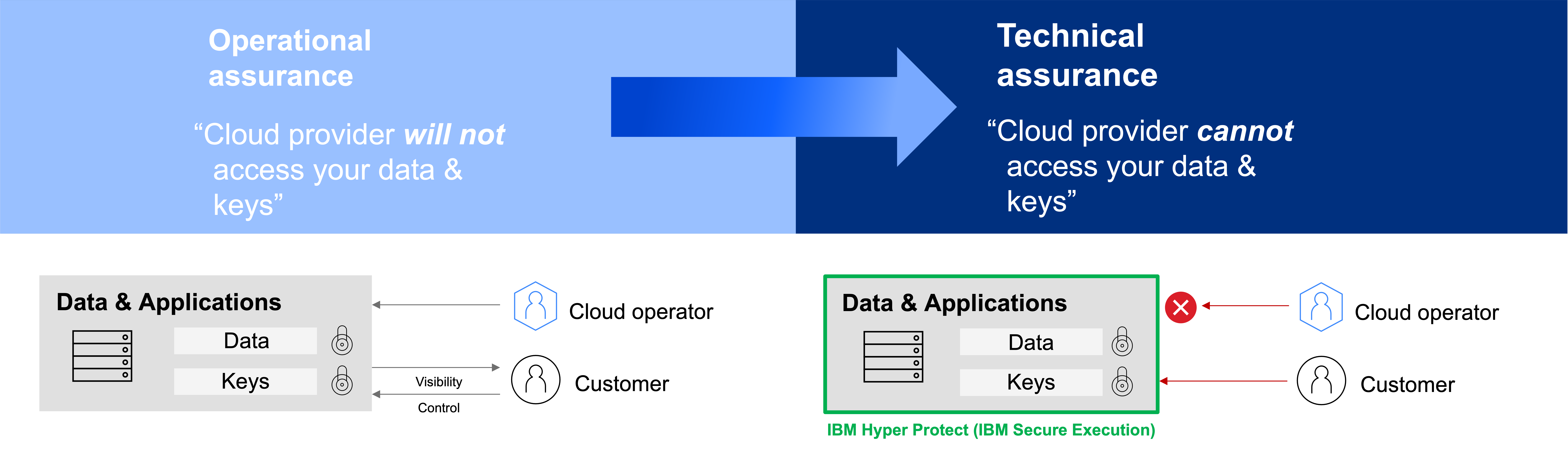
Computação confidencial is an emerging foundational capability that enables the protection of data-in-use. The protection of data-at-rest and data-in-motion has been a standard practice in the industry for decades; however, with advent of hybrid and decentralized management of infrastructure it has now become imperative to equally protect data-in-use. More specifically, confidential computing uses hardware-based security-rich enclaves to allow a tenant to host workloads and data on untrusted infrastructure while ensuring that their workloads and data cannot be read or modified by anyone with privileged access to that infrastructure. This is typically referred to as technical assurance that can summarily be described as a provider or person cannot access your data. One can contrast technical assurance to the more commonly used operational assurance that provides the lesser guarantee that a provider or person only promises they will not access your data, even though they technically could. As compromised credential threats as well as insider threats have become a dominant cause of data-security incidents, technical assurance has become a priority for securing sensitive and regulated workloads whether the latter are running in traditional on-premises or in a public cloud data centers.
IBM and RedHat have recognized the requirement for technical assurance in a hybrid cloud platform. They have worked as part of the Cloud Native Computing Foundation (CNCF) Confidential Containers open-source community to address this concern and are continuously working together to make confidential container technology available. The latter marries security-rich enclave technology such as IBM Secure Execution for Linux with Kubernetes-based OpenShift to allow for the deployment of containers into secured pods, providing all the advantages of a ubiquitous RH OCP operational experience while also designed to protect a tenant’s containers from privileged user access. Confidential containers go beyond prior efforts at solving this problem by isolating the container not only from infrastructure administrator but also from the Kubernetes administrator. This provides the tenant with the best of both worlds where they can fully leverage the abstraction of a managed OpenShift to develop-once-deploy-anywhere while being able to deploy data and workloads with technical assurance into a fully private and isolated enclave even if the latter is hosted and managed on third-party infrastructure.
IBM is further adding additional zero trust principles designed to increase security and ease of use with the IBM Hyper Protect Platform.

This unique capability is designed for workloads that have strong data sovereignty, regulatory or data privacy requirements.
As such, confidential containers play a key role across industries engineered to secure data and foster innovation. Some example use cases to highlight:
Confidential AI: leverage trustworthy AI and while ensuring the integrity of the models and confidentiality of data
Organizations leveraging AI models often encounter challenges related to the privacy and security of the data used for training and the integrity of the AI models themselves. Protecting the confidentiality of proprietary algorithms and sensitive training data is crucial. In many cases multiple party must collaborate and share sensitive data or models between each other to gain valuable AI-based insights. On the other hand, the valuable data needed to gain those insights has to stay confidential and is only allowed to be shared with certain parties or no third parties at all.
So, is there a way to gain insights of valuable data through AI without the need to expose the data set or the AI model (LLM, ML, DL) to another party?
Red Hat OpenShift, empowered by Confidential Containers based on IBM Secure Execution, provides a confidential AI platform. This safeguards both the AI model and the training data, allowing organizations to deploy machine learning models without compromising intellectual property or exposing sensitive information. By mitigating attack vectors through security-rich containers, Confidential Containers ensure the integrity of AI models, enhancing trust in AI applications.
Healthcare: enabling health tech while keeping patient data private
In the healthcare industry, the protection of sensitive patient data is paramount. With the increasing adoption of digital health records and collaborative research initiatives, there’s a growing concern about securing patient information from unauthorized access and potential breaches.
Red Hat OpenShift, leveraging Confidential Containers, establishes a security-rich enclave for healthcare applications. So that records and sensitive medical data are encrypted and processed securely, protecting against data leaks and unauthorized access. By safeguarding both the code and data, healthcare organizations are able to confidently embrace digital transformation while keeping their patients’ privacy by adopting data privacy-enhancing technologies, such as Confidential Compute.
This is designed to enable multiple use cases in the healthcare industry, one being secure multi-party collaboration between different institutions as shown in the following example.

Financial services: innovate customer experience while keeping sensitive information secure and stay compliant
Financial institutions face constant threats to their critical data and financial transactions. The industry demands a secure infrastructure that can protect sensitive financial information, prevent fraud and ensure regulatory compliance.
Red Hat OpenShift with confidential containers provides a fortified environment for financial services applications. This ensures that financial data and transactions are processed within security-rich enclaves, shielding them from external threats. By safeguarding code and data integrity, confidential containers on OpenShift helps financial institutions meet stringent regulatory requirements and enhances the overall security posture of their digital infrastructure.
Enhancing digital rights management and intellectual property protection through confidential compute-protected tokenization
In today’s digital landscape, the risk associated with stolen tokens or unauthorized signing of corresponding contracts, such as intellectual property and digital rights tokens, poses significant challenges. The potential financial losses and threats to the integrity of digital ecosystems demand a robust solution that goes beyond conventional security measures.
Confidential compute offers a practical solution to the risks associated with stolen tokens by incorporating confidential compute technology into the tokenization process, which is designed to establish end-to-end security. This approach ensures that sensitive operations occur in a secure and isolated environment, safeguarding the confidentiality and integrity of digital assets throughout their lifecycle. Confidential compute is engineered to prevent malicious actors from deciphering or manipulating sensitive information even if they gain access to the underlying infrastructure.
Implementing security-rich token platforms through confidential compute delivers tangible benefits. Digital rights holders can manage and monetize their intellectual property without the constant concern of piracy or unauthorized distribution. Stakeholders in various industries gain the ability to create, trade and enforce digital contracts with increased confidence in the security of their tokenized assets. Financial implications tied to token theft are significantly minimized, reducing the risk of revenue loss due to piracy or counterfeiting. This not only protects the economic interests of content creators and distributors but also promotes a more trustworthy digital ecosystem.
In conclusion, the adoption of confidential compute in the tokenization process addresses the crucial challenge of the expanding set of use cases from financial assets, real estate and to much larger scale tokens securing digital rights and intellectual property. The outcome is a shift towards more security-rich token platforms, providing content creators, distributors and consumers the confidence to engage in digital transactions while ensuring the sustained growth and integrity of the digital economy.
One example of growing use for tokens is online gaming. Confidential compute’s integration into tokenization safeguards in-game assets like virtual currencies and items. This is designed to promote heightened security, minimizing the financial risks and disruptions caused by stolen tokens in the dynamic landscape of online gaming.
Sovereign cloud: enhance data security to enable data privacy and sovereignty
National security and data sovereignty concerns drive the need for a secure hybrid cloud infrastructure that is designed to ensure that critical data and applications are not subject to unauthorized access or foreign jurisdiction.
Red Hat OpenShift, with confidential container capabilities, supports the implementation of sovereign clouds. By establishing secure containers, it enables nations to host critical applications and data within a protected environment, promoting data sovereignty and protecting against external threats. This solution provides a trusted platform for government agencies and critical infrastructure, fostering national security in the digital age.
Zero Trust SaaS: succeed at your SaaS transformation while keeping your client’s data private by applying built-in zero trust principles
As a SaaS provider aiming to offer scalable solutions to target customers with sensitive data or regulatory requirements, the challenge lies in providing cloud-based services without compromising the security and confidentiality of clients’ data. The need for a comprehensive Zero Trust framework becomes crucial to assure clients that their sensitive information remains inaccessible, not only by the SaaS provider but also by the underlying cloud infrastructure.
Red Hat OpenShift, fortified with confidential containers and integrated with Zero Trust as a service, revolutionizes the approach to Zero Trust SaaS from the provider’s standpoint. This solution helps that the SaaS provider, the cloud provider, IaaS Admin, and Kubernetes Admin have zero access to clients’ data.
The absence of isolation between different clusters within the cloud environment not only helps to optimize costs but also streamlines operational efficiency. Simultaneously, the isolation at the pod level within each cluster’s namespace enhances security, contributing to reduced certification audit efforts and reinforcing the SaaS provider’s commitment to data integrity.
Moreover, the implementation of multi-party Zero Trust allows clients and 4th party ISVs to run confidential workloads as containers without direct access to the underlying data. This innovative approach not only meets the stringent security requirements of clients but also positions the SaaS provider as a trusted partner capable of delivering scalable and security-rich solutions for clients with sensitive data or regulatory constraints.
Learn more about Confidential Compute with IBM Secure Execution on IBM LinuxONE
Mais da nuvem híbrida




Boletins informativos da IBM
Receba nossos boletins informativos e atualizações de tópicos que oferecem as mais recentes lideranças inovadoras e insights sobre tendências emergentes.
Inscreva-se agora
Mais boletins informativos
- Conteúdo com tecnologia de SEO e distribuição de relações públicas. Seja amplificado hoje.
- PlatoData.Network Gerativa Vertical Ai. Capacite-se. Acesse aqui.
- PlatoAiStream. Inteligência Web3. Conhecimento Amplificado. Acesse aqui.
- PlatãoESG. Carbono Tecnologia Limpa, Energia, Ambiente, Solar, Gestão de resíduos. Acesse aqui.
- PlatoHealth. Inteligência em Biotecnologia e Ensaios Clínicos. Acesse aqui.
- Fonte: https://www.ibm.com/blog/confidential-containers-with-red-hat-openshift-container-platform-and-ibm-secure-execution-for-linux/
- :tem
- :é
- :não
- :onde
- 1
- 10
- 12
- 15%
- 1800
- 2019
- 2023
- 2024
- 203
- 29
- 30
- 300
- 31
- 40
- 400
- sec 4
- 9
- a
- habilidade
- Capaz
- Sobre
- RESUMO
- abstração
- abundância
- Acesso
- em
- atores
- acrescentando
- Adicional
- endereço
- endereços
- admin
- Adotando
- Adoção
- vantagens
- advento
- Publicidade
- contra
- idade
- agências
- agregar
- AI
- Modelos de IA
- Plataforma de IA
- Visando
- algoritmos
- alinhar
- Todos os Produtos
- permitir
- permitidas
- Permitindo
- permite
- tb
- entre
- amp
- an
- analítica
- e
- Outro
- qualquer um
- APIs
- app
- Aplicação
- Desenvolvimento de Aplicações
- aplicações
- Aplicando
- abordagem
- SOMOS
- ÁREA
- artigo
- AS
- avaliação
- Ativos
- associado
- garantia
- assegurar
- At
- ataque
- auditor
- autor
- automatizando
- disponível
- longe
- em caminho duplo
- baseado
- Batalha
- BE
- tornam-se
- torna-se
- sido
- ser
- Benefícios
- MELHOR
- entre
- Pós
- Blog
- Blogs
- Azul
- ambos
- violações
- Break
- construir
- construído
- construídas em
- negócio
- negócios
- mas a
- botão
- by
- CAN
- não podes
- capacidades
- capacidade
- capaz
- carbono
- cartão
- Cartões
- casos
- CAT
- Categoria
- Causar
- causado
- Centros
- certo
- FDA
- desafiar
- desafios
- verificar
- Escolha
- círculos
- CIS
- classe
- remover filtragem
- cliente
- clientes
- Fechar
- Na nuvem
- infraestrutura de nuvem
- Nativo da nuvem
- Plataforma em nuvem
- código
- colaborar
- colaboração
- colaborativo
- colegas
- cor
- vem
- compromisso
- comum
- geralmente
- comunidade
- Empresas
- integrações
- complexidade
- compliance
- componentes
- compreensivo
- Comprometido
- comprometendo
- Computar
- computador
- computação
- Interesse
- Preocupações
- conclusão
- confiança
- confidencialidade
- com confiança
- constante
- restrições
- Consumidores
- Recipiente
- Containers
- conteúdo
- criadores de conteúdo
- contexto
- continuar
- continua
- contínuo
- continuamente
- contratos
- contraste
- contribuindo
- ao controle
- convencional
- Correspondente
- custos
- falsificação
- coberto
- crio
- Criar
- criadores
- CREDENCIAL
- crítico
- Infraestrutura crítica
- crucial
- APF
- moedas
- Atual
- personalizadas
- cliente
- experiência do cliente
- Clientes
- ciclo
- dados,
- centros de dados
- gestão de dados
- privacidade de dados
- segurança dos dados
- conjunto de dados
- data warehouse
- Data
- décadas
- Dezembro
- Descentralizada
- Padrão
- definições
- entregar
- entregando
- entrega
- Demanda
- demandas
- Dependência
- implantar
- desenvolvimento
- descrito
- descrição
- projetado
- Developer
- Desenvolvimento
- Dispositivos/Instrumentos
- DevOps
- diagnosticar
- diferente
- digital
- idade digital
- Ativos Digitais
- Economia digital
- ecossistema digital
- Digital Health
- direitos digitais
- transações digitais
- Transformação Digital
- diretamente
- Acesso direto
- desapontamento
- interrupções
- Distinto
- distribuição
- distribuidores
- diferente
- dns
- distância
- dois
- dinâmico
- cada
- facilidade
- facilidade de utilização
- fácil
- Econômico
- economia
- ecossistema
- ecossistemas
- efetivamente
- eficiência
- esforços
- abraços
- abraçando
- emergiu
- emergência
- emergente
- habilitada
- permitir
- permite
- permitindo
- enclave
- encontro
- criptografada
- final
- end-to-end
- aplicar
- engajar
- engenharia
- aumentar
- Melhora
- aprimorando
- garantir
- garante
- assegurando
- Entrar
- Empreendimento
- Meio Ambiente
- ambientes
- igualmente
- especialmente
- essencial
- estabelecer
- estabelece
- estabelecendo
- propriedade
- Éter (ETH)
- Mesmo
- exemplo
- execução
- saída
- expansão
- expectativas
- vasta experiência
- se estende
- externo
- Rosto
- falso
- poucos
- financeiro
- dados financeiros
- informação financeira
- Instituições financeiras
- serviços financeiros
- descoberta
- Flexibilidade
- focando
- seguir
- seguinte
- fontes
- Escolha
- forçando
- estrangeiro
- Forrester
- fortificado
- Promover
- fomento
- Foundation
- Fundacional
- Quadro
- fraude
- Freedom
- da
- totalmente
- mais distante
- futuro
- Ganho
- jogos
- Gartner
- gerador
- ter
- Go
- vai
- Governo
- agências governamentais
- Grade
- Crescente
- Growth
- garanta
- mão
- chapéu
- Ter
- Título
- Saúde
- Tecnologia em Saúde
- saúde
- setor de saúde
- altura
- intensificada
- ajuda
- Destaques
- altamente
- titulares
- hospedeiro
- hospedado
- hospedagem
- Como funciona o dobrador de carta de canal
- Como Negociar
- Contudo
- HTTPS
- HÍBRIDO
- Nuvem híbrida
- Hype
- IBM
- ICO
- ÍCONE
- if
- imagem
- imagens
- imperativo
- implementação
- implicações
- in
- in-game
- inacessível
- incorporando
- Crescimento
- aumentou
- aumentando
- índice
- indústrias
- indústria
- INFORMAÇÕES
- Infraestrutura
- infra-estrutura
- Inicia
- iniciativas
- inovar
- Inovação
- inovadores
- Informante
- insights
- instâncias
- instituições
- integrado
- integração
- integridade
- intelectual
- propriedade intelectual
- proteção da propriedade intelectual
- interesses
- para dentro
- intricado
- intrínseco
- introduzido
- isolado
- isolamento
- questões
- IT
- Unid
- ESTÁ
- janeiro
- Java
- Trabalho
- jpg
- jurisdição
- manutenção
- Chave
- Kubernetes
- paisagem
- grande
- Maior
- Sobrenome
- Ano passado
- mais recente
- Liderança
- principal
- Vazamentos
- aprendizagem
- levou
- menor
- Nível
- Alavancagem
- aproveitando
- Liberty
- encontra-se
- wifecycwe
- como
- linux
- local
- local
- locais
- fora
- perdas
- máquina
- aprendizado de máquina
- fazer
- malicioso
- gerencia
- gerenciados
- de grupos
- Gerente
- gestão
- manipulando
- muitos
- Março
- maciço
- max-width
- Posso..
- medidas
- médico
- dados médicos
- Conheça
- reunião
- atende
- malha
- microsserviços
- migrado
- migrando
- minutos
- minimizar
- minimizando
- minutos
- mitigando
- ML
- Móvel Esteira
- modelo
- modelos
- EQUIPAMENTOS
- modificada
- Monetizar
- monitoração
- mais
- a maioria
- mover
- muito
- multipartidário
- múltiplo
- devo
- Nacional
- segurança nacional
- Das Nações
- nativo
- Navegação
- você merece...
- necessário
- rede
- networking
- Novo
- newsletters
- não
- nada
- agora
- Nuança
- ocorrer
- of
- WOW!
- oferecer
- Oferece
- frequentemente
- on
- ONE
- online
- jogo on line
- só
- aberto
- open source
- operacional
- Operações
- Otimize
- otimizado
- or
- organizações
- Outros
- A Nossa
- Resultado
- Acima de
- global
- página
- Supremo
- parte
- partes
- parceiro
- festa
- paciente
- dados do paciente
- Pico
- atuação
- pessoa
- PHP
- Pirataria
- colocado
- plataforma
- Plataformas
- platão
- Inteligência de Dados Platão
- PlatãoData
- Jogar
- plug-in
- vagens
- Privacidade
- coloca
- posição
- abertas
- Publique
- potencial
- Prática
- prática
- presente
- evitar
- primário
- princípios
- Prévio
- prioridade
- política de privacidade
- Privacidade e segurança
- privado
- privilegiado
- Problema
- processo
- processado
- a promover
- promove
- Promoção
- propriedade
- proprietário
- proteger
- protegido
- proteger
- proteção
- protege
- provedor
- fornece
- fornecendo
- público
- nuvem pública
- Leia
- Leitura
- reais
- bens imóveis
- reino
- recentemente
- reconhecido
- registros
- recuperação
- Vermelho
- Red Hat
- Reduzido
- redução
- a que se refere
- refletir
- regulamentadas
- reguladores
- Conformidade Regulamentar
- relacionado
- permanece
- pedidos
- requerimento
- Requisitos
- exige
- pesquisa
- responsivo
- DESCANSO
- receita
- revoluciona
- certo
- direitos
- ascensão
- Risco
- riscos
- robôs
- uma conta de despesas robusta
- Tipo
- Execute
- corrida
- SaaS
- salvaguardando
- proteções
- escalável
- Escala
- Peneira
- Scripts
- seguro
- Secured
- firmemente
- assegurando
- segurança
- Medidas de Segurança
- parece
- sensível
- seo
- servidor
- serviço
- Serviços
- conjunto
- Partilhar
- compartilhado
- mudança
- Baixo
- mostrando
- periodo
- de forma considerável
- assinatura
- simples
- simultaneamente
- local
- Habilidades
- pequeno
- So
- Software
- solução
- Soluções
- Resolvendo
- alguns
- soberano
- soberania
- específico
- especificamente
- Patrocinado
- primavera
- bota de mola
- quadrados
- partes interessadas
- padrão
- ponto de vista
- começo
- Estado
- ficar
- direcção
- Passos
- roubado
- estratégias
- Simplifica
- rigoroso
- mais forte,
- sujeito
- Inscreva-se
- suceder
- tal
- ajuda
- Apoiar
- suportes
- telhado
- SVG
- tangível
- Target
- tecnologia
- Dados Técnicos:
- tecnicamente
- Tecnologias
- Tecnologia
- inquilino
- terciário
- que
- A
- O Futuro
- O Estado
- o mundo
- roubo
- deles
- Eles
- tema
- si mesmos
- Lá.
- Este
- deles
- Terceiro
- terceiro
- De terceiros
- isto
- aqueles
- Apesar?
- pensamento
- liderança de pensamento
- ameaças
- Através da
- todo
- Amarrado
- tempo
- Título
- para
- hoje
- juntos
- token
- tokenization
- tokenized
- ativos tokenized
- Tokens
- tolerância
- topo
- tópico
- toca
- para
- comércio
- tradicional
- tradicionalmente
- tráfego
- Training
- Transações
- Transformação
- Tendências
- verdadeiramente
- Confiança
- Estrutura de CONFIANÇA
- confiável
- parceiro de confiança
- digno de confiança
- tipo
- tipos
- tipicamente
- onipresente
- não autorizado
- subjacente
- por baixo
- sustentar
- único
- Atualizações
- URL
- usar
- usava
- Utilizador
- usos
- Valioso
- valor
- vário
- versão
- Virtual
- moedas virtuais
- W
- queremos
- Armazém
- Armazenagem
- Caminho..
- BEM
- se
- qual
- enquanto
- porque
- precisarão
- de
- dentro
- sem
- WordPress
- trabalhou
- fluxos de trabalho
- trabalhar
- mundo
- do mundo
- escrito
- ano
- Você
- investimentos
- zefirnet
- zero
- zero confiança